Achtung: Trojaner! Fwd: SACOMBANK GỬI ĐIỆN THANH TOÁN SWIFT PAYMENTS von Nghiem Thi Huyen ([email protected])
Am Donnerstag, den 14. September 2017 wurde durch unbekannte Dritte die folgende E-Mail in vietnamesischer Sprache versendet. Achtung: Es handelt sich um eine gefälschte E-Mail! Das beigefügte ZIP-Archiv enthält ein Trojanisches Pferd. Klicken Sie daher nicht auf den Anhang und Öffnen Sie diesen nicht!
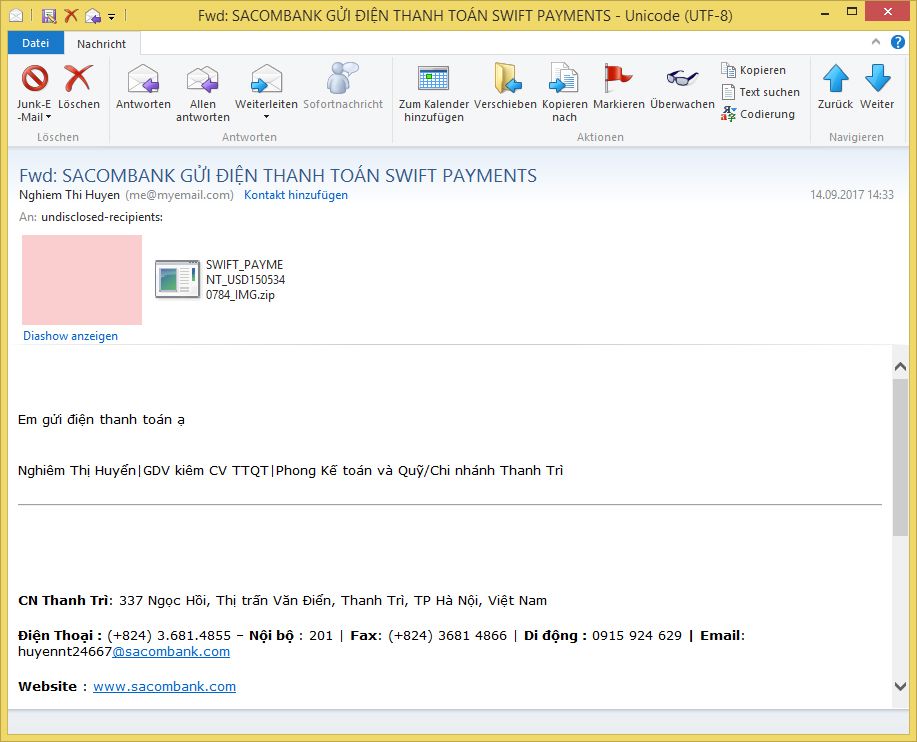
Fwd: SACOMBANK GỬI ĐIỆN THANH TOÁN SWIFT PAYMENTS
Nghiem Thi Huyen ([email protected])Em gửi điện thanh toán ạ
Nghiêm Thị Huyển|GDV kiêm CV TTQT|Phong Kế toán và Quỹ/Chi nhánh Thanh Trì
——————————————————————————–
CN Thanh Trì: 337 Ngọc Hồi, Thị trấn Văn Điển, Thanh Trì, TP Hà Nội, Việt Nam
Điện Thoại : (+824) 3.681.4855 – Nội bộ : 201 | Fax: (+824) 3681 4866 | Di động : 0915 924 629 | Email: [email protected]
Website : www.sacombank.com
Achtung: Es handelt sich um eine gefälschte E-Mail! Mit der Nachricht wird keine SWIFT-Zahlung angekündigt! Öffnen Sie daher nicht die Anlage!
Die E-Mail kommt mit zwei Dateien. Ein Bild („blocked.gif“) und ein ZIP-Archiv („SWIFT_PAYMENT_USD1505340784_IMG.zip“). Das ZIP-Archiv enthält eine Java-Anwendung:
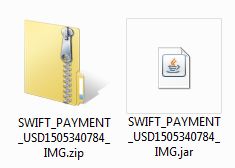
SWIFT_PAYMENT_USD1505340784_IMG.zip
SWIFT_PAYMENT_USD1505340784_IMG.jar
Laut Virustotal liegt die Erkennungsrate für die .jar-Datei bei 7/58: Java/Jrat.AW bzw. Trojan.Java.Adwind. Führen Sie die Datei daher nicht aus! Es handelt sich um eine bösartige Software!
Die Anwendung würde u. a. Analyse-Tool beenden, damit ihr Verhalten nicht protokolliert werden kann. Auf dem System werden verschiedene Dateien angelegt, darunter u. a. diverse .class-Dateien:
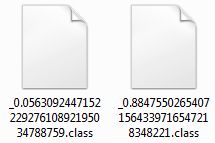
_0.056309244715222927610892195034788759.class
_0.88475502654071564339716547218348221.class
Laut Virustotal liegt die Erkennungsrate für die .class-Dateien bei 42/59!
Außerdem wird mindestens eine .dll-Datei hinzufgefügt:
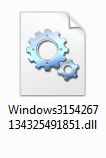
Windows3154267134325491851.dll
Laut Virustotal liegt die Erkennungsrate für die .dll-Datei bei 42/64!
Neben den o. g. Dateien werden mindestens zwei Verzeichnisse angelegt, in die eine oder mehrere Dateien gelegt werden:
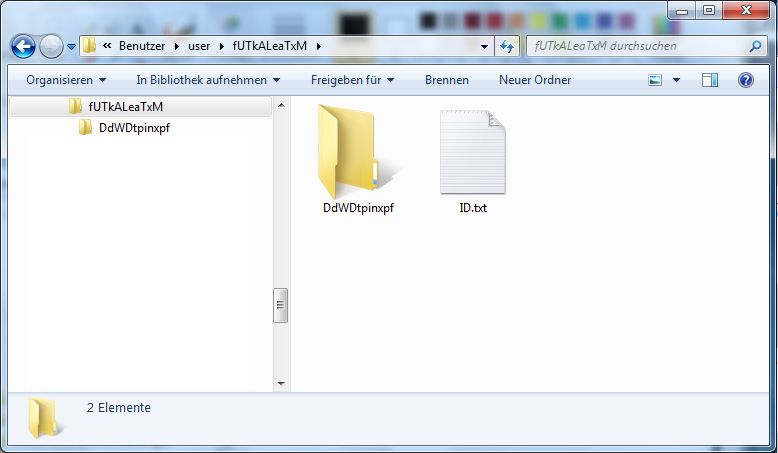
DdWDtpinxpf
ID.txt
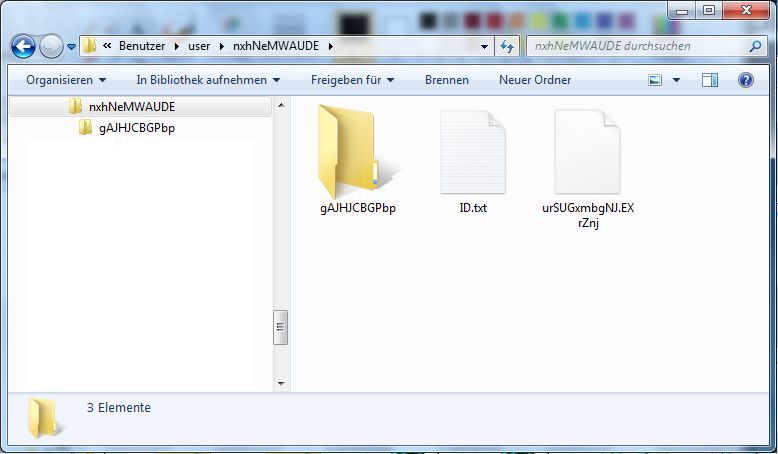
gAJHJCBGPbp
ID.txt
urSUGxmbgNJ.EXrZnj
In der Registry wird ein Eintrag angelegt, damit der Trojaner bei jedem PC-Start ausgeführt wird:
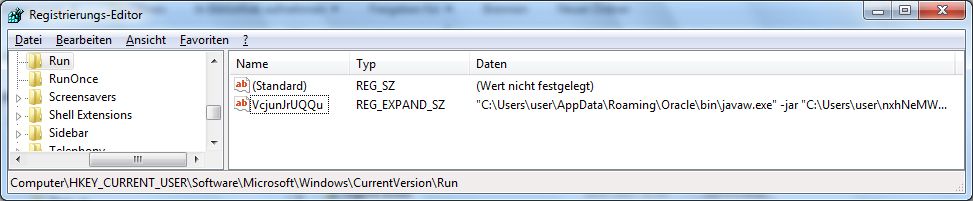
Schlüsselname: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
Name: VcjunJrUQQu
Daten: „C:\Users\user\AppData\Roaming\Oracle\bin\javaw.exe“ -jar „C:\Users\user\nxhNeMWAUDE\urSUGxmbgNJ.EXrZnj“
Außerdem importiert der Trojaner auch eine .reg-Datei in die Registry:
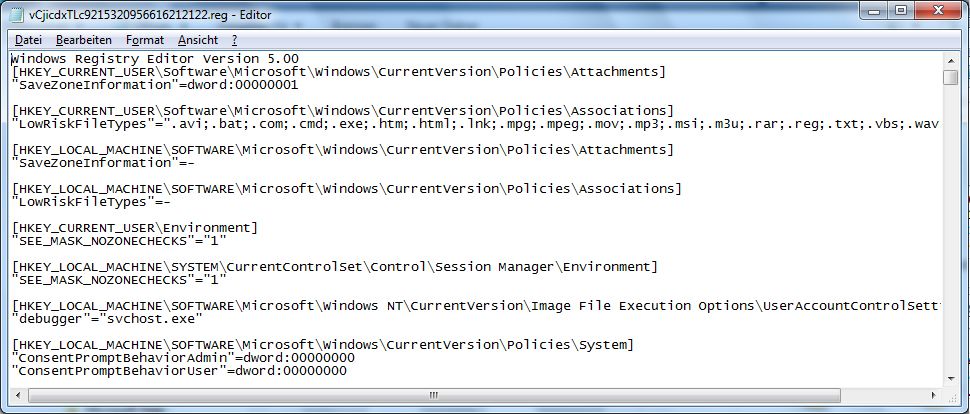
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments]
„SaveZoneInformation“=dword:00000001[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations]
„LowRiskFileTypes“=“.avi;.bat;.com;.cmd;.exe;.htm;.html;.lnk;.mpg;.mpeg;.mov;.mp3;.msi;.m3u;.rar;.reg;.txt;.vbs;.wav;.zip;.jar;“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Attachments]
„SaveZoneInformation“=-[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Associations]
„LowRiskFileTypes“=-[HKEY_CURRENT_USER\Environment]
„SEE_MASK_NOZONECHECKS“=“1“[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Environment]
„SEE_MASK_NOZONECHECKS“=“1“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\UserAccountControlSettings.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System]
„ConsentPromptBehaviorAdmin“=dword:00000000
„ConsentPromptBehaviorUser“=dword:00000000
„EnableLUA“=dword:00000000
„PromptOnSecureDesktop“=dword:00000000[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Taskmgr.exe]
„debugger“=“svchost.exe“[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System]
„DisableTaskMgr“=dword:00000002[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\SystemRestore]
„DisableConfig“=dword:00000001
„DisableSR“=dword:00000001[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ProcessHacker.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\procexp.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MSASCui.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MsMpEng.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpUXSrv.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpCmdRun.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\NisSrv.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ConfigSecurityPolicy.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\procexp.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wireshark.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tshark.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\text2pcap.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rawshark.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mergecap.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\editcap.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\dumpcap.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\capinfos.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mbam.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mbamscheduler.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mbamservice.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AdAwareService.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AdAwareTray.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\WebCompanion.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AdAwareDesktop.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\V3Main.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\V3Svc.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\V3Up.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\V3SP.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\V3Proxy.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\V3Medic.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\BgScan.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\BullGuard.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\BullGuardBhvScanner.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\BullGuarScanner.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\LittleHook.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\BullGuardUpdate.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\clamscan.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ClamTray.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ClamWin.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cis.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\CisTray.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmdagent.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cavwp.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\dragon_updater.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MWAGENT.EXE]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MWASER.EXE]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\CONSCTLX.EXE]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avpmapp.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\econceal.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\escanmon.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\escanpro.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TRAYSSER.EXE]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TRAYICOS.EXE]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\econser.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\VIEWTCP.EXE]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FSHDLL64.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\fsgk32.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\fshoster32.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FSMA32.EXE]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\fsorsp.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\fssm32.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FSM32.EXE]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\trigger.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FProtTray.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FPWin.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FPAVServer.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVK.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\GdBgInx64.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVKProxy.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\GDScan.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVKWCtlx64.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVKService.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVKTray.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\GDKBFltExe32.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\GDSC.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\virusutilities.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\guardxservice.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\guardxkickoff_x64.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\iptray.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\freshclam.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\freshclamwrap.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\K7RTScan.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\K7FWSrvc.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\K7PSSrvc.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\K7EmlPxy.EXE]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\K7TSecurity.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\K7AVScan.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\K7CrvSvc.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\K7SysMon.Exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\K7TSMain.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\K7TSMngr.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nanosvc.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nanoav.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nnf.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nvcsvc.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nbrowser.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nseupdatesvc.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nfservice.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nwscmon.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\njeeves2.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nvcod.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nvoy.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\zlhh.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Zlh.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nprosec.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Zanda.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\NS.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\acs.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\op_mon.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PSANHost.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PSUAMain.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PSUAService.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AgentSvc.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\BDSSVC.EXE]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\EMLPROXY.EXE]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\OPSSVC.EXE]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ONLINENT.EXE]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\QUHLPSVC.EXE]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SAPISSVC.EXE]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SCANNER.EXE]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SCANWSCS.EXE]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\scproxysrv.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ScSecSvc.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SUPERAntiSpyware.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SASCore64.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SSUpdate64.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SUPERDelete.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SASTask.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\K7RTScan.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\K7FWSrvc.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\K7PSSrvc.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\K7EmlPxy.EXE]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\K7TSecurity.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\K7AVScan.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\K7CrvSvc.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\K7SysMon.Exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\K7TSMain.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\K7TSMngr.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\uiWinMgr.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\uiWatchDog.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\uiSeAgnt.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PtWatchDog.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PtSvcHost.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PtSessionAgent.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\coreFrameworkHost.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\coreServiceShell.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\uiUpdateTray.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\VIPREUI.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SBAMSvc.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SBAMTray.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SBPIMSvc.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bavhm.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\BavSvc.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\BavTray.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Bav.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\BavWebClient.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\BavUpdater.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MCShieldCCC.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MCShieldRTM.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MCShieldDS.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MCS-Uninstall.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SDScan.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SDFSSvc.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SDWelcome.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SDTray.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\UnThreat.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\utsvc.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FortiClient.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\fcappdb.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FCDBlog.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FCHelper64.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\fmon.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FortiESNAC.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FortiProxy.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FortiSSLVPNdaemon.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FortiTray.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FortiFW.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FortiClient_Diagnostic_Tool.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\av_task.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\CertReg.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FilMsg.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\FilUp.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\filwscc.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\filwscc.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\psview.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\quamgr.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\quamgr.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\schmgr.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\schmgr.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\twsscan.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\twssrv.exe]
„debugger“=“svchost.exe“[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\UserReg.exe]
„debugger“=“svchost.exe“